
At one level or another, the user has to decide that the guarantees of security, privacy or identity offered is "good enough" for the purposes on hand.
Therefore, the design of the trust model is an important criterion of the cryptosystem chosen.
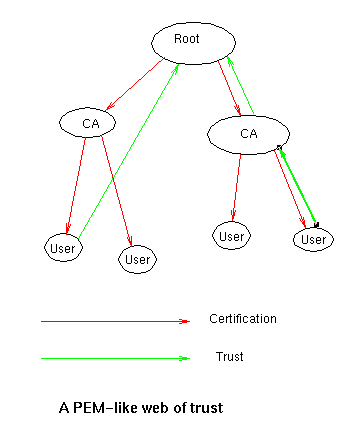
The basic idea in a treelike trust model is that users need to trust a few entities only, and that these should be special entities created for that purpose, who can be relied upon to manage their keys in a respectable fashion.
To faciliate easily finding a path of certificates from someone the user trusts to any other user, the model suggests using one or more "root certification authorities", who in turn certify subordinate certification authorities, who (at some level) certify users.
In this model,it is easy to find out whether someone's certificate is valid or not; just ask the relevant CA if it has been revoked.
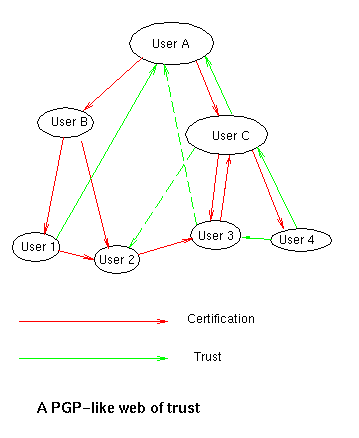
In the weblike model, there are no certification authorities per se; all there is are users. Any of them may certify any other, and may trust any other to any appropriate degree.
In such a mesh, user 1 may trust user B's identity because user A has certified it; user 3 has only limited faith in user B's identity because his trust in user A is not so strong, and will wait for corroboration from user 2 before trusting in B's identity.
Revoking an identity in such a mesh is a bit harder; if user 3 finds that his key has been compromised, and tells user C to revoke the certificate he issued, it may still be trusted by user 1 because of the independent path through user 2, which user 3 may have forgotten all about.
Still, the PGP experience has shown us that building such a web of trust within a small community is much easier than finding, designating, staffing and getting trust in an authority with the power of issuing certificates for the same group.
In the PGP model, this has been established by usage: The key certificate means that the signer believes that the name string presented together with the public key is a reasonable name for the entity who claims to have the corresponding private key.
In the PEM model, the certificate means that the certification authority has done what its policy says before issuing the certificate; this may commonly involve chekcking a person's ID card or similar identity checks. Again, only identity is involved.
In a commercial model, one might want a certificate to mean that "this person has an account with our bank, and we are willing to bet up to NOK 5000 that he is able to cover whatever promises of payment he makes to you", or "this person is allowed to issue purchase orders for up to NOK 100.000 on behalf of the company".
The encoding of such information inside a certificate is the subject of active study now, and will probably be clarified much more within a year or so.